CVE-2020-26894 Privilege Escalation Vulnerability in LiveCode v9.6.1 Programming Language
Summary
LiveCode v9.6.1 for Windows is vulnerable to a horizontal privilege escalation vulnerability.
CVE Mitre Assigned: CVE-2020-26894
Discovery
While taking a Wildlife Issues course at my University, I discovered a high severity vulnerability in the course software our class was using that leads to a horizontal privilege escalation.
At first, I thought the vulnerability was only in this course software, but looking into it deeper and with the help of one of the developers at faulkner press, we discovered that the vulnerability actually lied in the programming language/framework they were using: LiveCode.
For those who aren’t familiar, LiveCode is a high-level scripting language belonging to the family of xTalk scripting languages along side HypderCard’s HyperTalk, allowing you to build cross-platform applications with relative ease.
Vulnerability
LiveCode has a function called “shell()” which, as you would expect, allows you to run shell commands and store its output. Most high-level programming languages that have a similar shell command function will use the environment variable %COMSPEC in Windows to determine the location of the shell to use to run the command, unless otherwise specified by the programmer. For Linux, it will usually use “/bin/sh”.
LiveCode v9.6.1, however, does not reference %COMSPEC when attempting to locate cmd.exe to run the “shell()” function. This is dangerous, since it means it will follow the command search sequence. This will force the application to check the current directory of the application for cmd.exe before checking %PATH.
This means that if the folder the application is running in is world writable (such as being installed in the root drive), then a low privileged user can create a malicious cmd.exe in that folder, which will be executed every time the application is started by any user on the system, and will assume the privileges of that user. This is known as horizontal privilege escalation.
After contacting LiveCode, the vulnerability has been patched in LiveCode 9.6.2-rc-1
LiveCode Bug Report: https://quality.livecode.com/show_bug.cgi?id=22942
CVE Mitre Assigned: CVE-2020-26894
Workaround
For those who need a workaround and can’t update, use the following command to tell the “shell()” function to use C:\Windows\System32\cmd.exe
set the shellCommand to "C:\Windows\System32\cmd.exe"
Proof-of-Concept
The following is code that is vulnerable to cmd.exe hijacking:
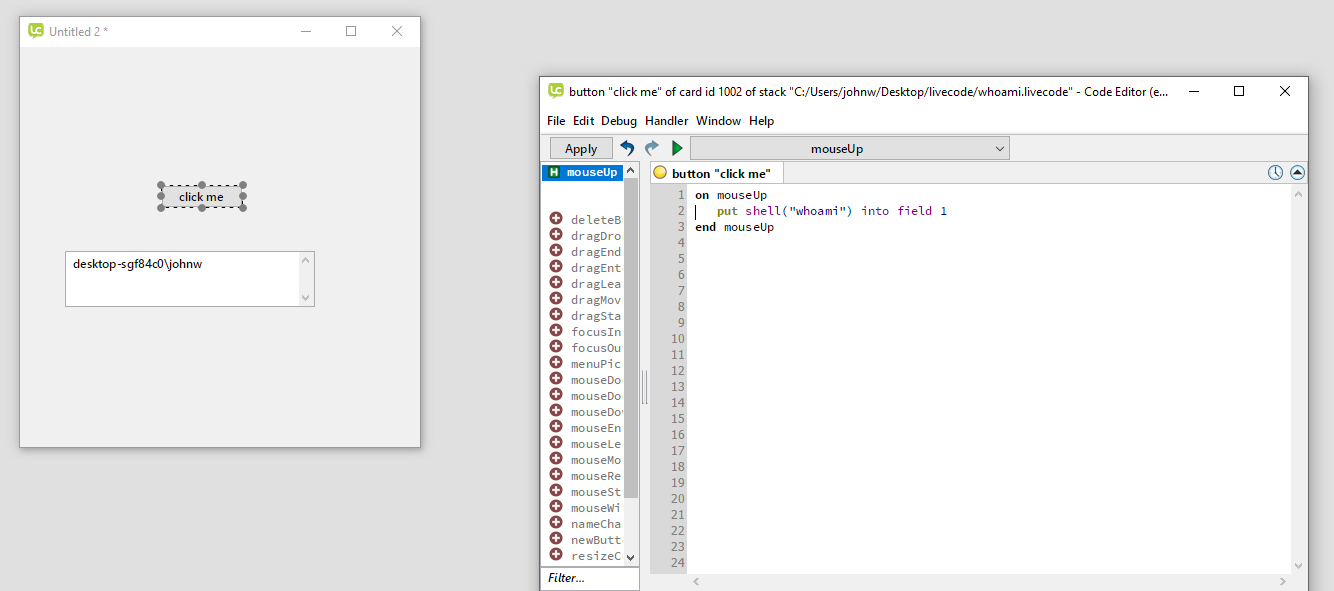
As you can see below, procmon shows that the vulnerable application is attempting to first get “cmd.exe” from the folder the application is running in before using C:\Windows\System32\cmd.exe.
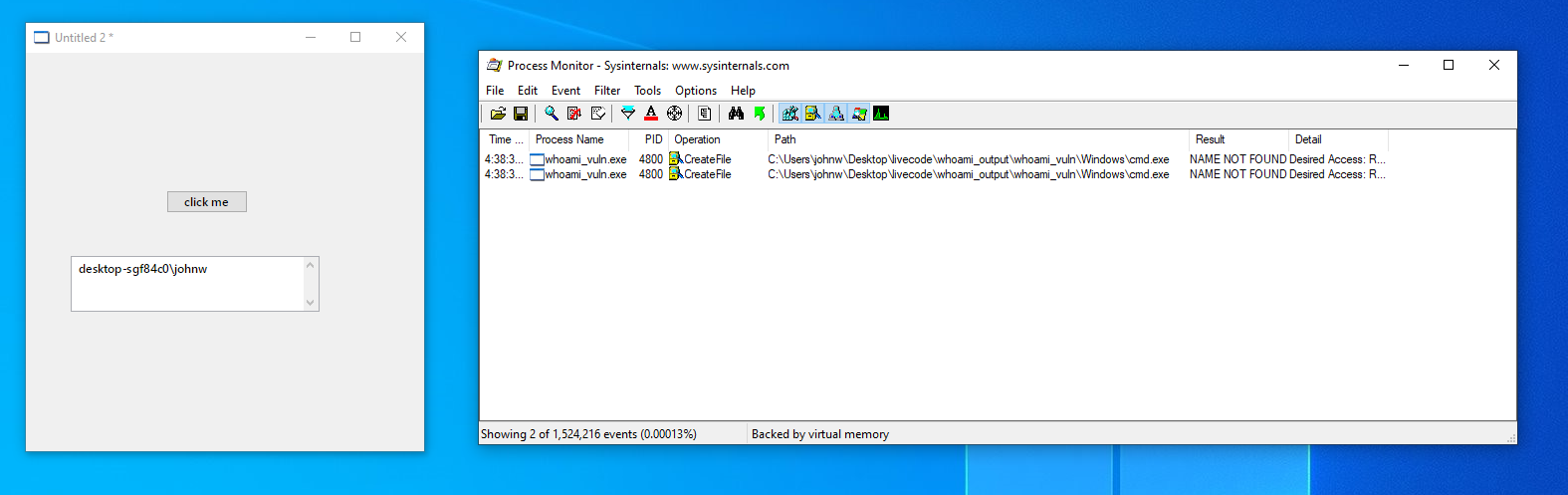
And below is a PoC exploitation of the vulnerable application to pop calc by simply copying calc.exe into the folder of the application and naming it cmd.exe.